Impersonation scams can be a major threat to businesses. Impersonation scams usually involve cybercriminals copying business owners and other employees through the use of phishing emails(check our blog on phishing emails to learn more!). Cybercriminals usually try to trap victims into performing money transfers, paying invoices, or sending the attacker sensitive data. Luckily, there are some measures you can take to protect your business.
Trusted reports regarding phishing email stats show that over 3.4 billion emails sent daily in 2022 are part of phishing attacks. That would mean over a trillion phishing emails get sent out yearly! It is one of the most severe and widespread types of cybercrime. The good news is that there are ways you can take action in protecting your business from these attacks. This article explains why and how.
EMAIL IMPERSONATION ATTACKS RELY ON SPOOFING
Email spoofing is when the sender of an email, typically spam, forges (spoofs) the email header “From” address so the email being sent appears to have been sent from a legitimate email address that is not the spammers own address.
They do this for a couple of reasons:
- To trick spam filters into allowing the email through by using a reputable email address. This would be one way your friends and family would see spam emails from you in their Inbox, rather than their spam folder.
- To prevent the bounce back emails from being received in the spammer’s own inbox. Spammers may send their spam out to thousands of email addresses, and inevitably a lot of those emails are going to bounce. Since spammers don’t want to receive hundreds of bounce back messages, this prevents that from happening.
MECHANISMS OF SPOOFED EMAILS:
There are two commonly used impersonation methods. To show these methods we will be “impersonating” Jane Doe.
Method #1 – Display Name Spoofing: Only Jane’s name will be spoofed, but not the email address: Jane Doe <jane_doe7639@gmail.com>.

Method #2 – Email Address Spoofing: Jane’s email address and her name are spoofed on an incoming email. Jane Doe <jane-doe@sgassociates.com>
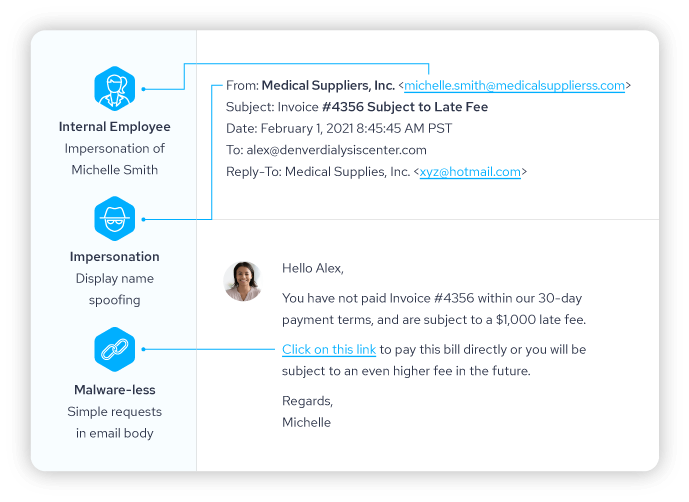
With web-based free email available, method 1 is a pretty simple attack to carry out. All the attacker needs is the name of somebody in your business. They will use public information such as LinkedIn or your website to find someone in a certain position of authority to target. All that’s left to do is sign up with a free email service provider such as Gmail, Outlook.com or Yahoo Mail using that name.
Good news is that your staff can make simple changes to your email service to protect yourselves from these methods listed above.
PREVENTING METHOD #1
Although Display Name Spoofing is a less sophisticated technique than email spoofing, it is much more difficult to prevent. Since the email address is technically valid these messages will slip through the cracks and won’t be detected with anti spam filtering, SPF, DKIM and DMARC. Your first and last line of defense are the employees. Being able to recognize these emails are important.
With Method #1 cybercriminals simply register a new email address with a free email provider using the same name as an executive from your organization (e.g. Saul Goodman saul.goodman1337@gmail.com). Technically, the email address is valid, so emails sent from these accounts will slip through anti-spam filtering. Similarly, the SPF/DKIM/DMARC records will not block these phishing emails either, because the email address is not forged.
Display Name Spoofing attacks are not stopped by regular anti-spam filters
As a result, the first and last line of defence is your employees. They need to be vigilant and be prepared to identify emails using the Display Name Spoofing technique. Sadly, this is prone to human error as your employees may not verify the full details of every single incoming email under certain circumstances – like in stressful situations such as fast-approaching deadlines or lack of attention to detail.
Also, employees may believe that because the email looks like it has come from someone they are familiar with and with the standard company email signature signoff from that person, that the email is legitimate. Unfortunately, attackers can also use the same email signatures at the bottom of emails sign-offs as legitimate senders.
To add insult to injury, many email clients – especially smartphone email clients – only display the sender’s name by default, but not the email address. For example, the Mail app on the iPhone requires you to tap on the sender’s name to reveal an email address.
Not all smartphone email clients display the sender address by default
Employees should be trained to identify deceptive emails with the forged display names and should receive as many visual aids as possible to detect if something is off. Luckily, Office 365 and G Suite can be configured to help combat display name spoofing by providing employees with visual clues.
PREVENTING METHOD #2
Did you know that every email has two different senders? One email address is called the ‘envelope sender’, and the other is set in the email header. The latter is known as the ‘From:’ header, which is normally displayed by the email clients, like Microsoft Outlook. Unfortunately, cybercriminals can forge the ‘From:’ header to trick email clients into displaying a name and email address which belong to your business.
You or your IT staff can make changes to your email service settings to help block deceptive emails coming into your organization, and put other email services on notice as to what a legitimate email coming from you should look like. This is done by adding what is known as SPF, DKIM and DMARC DNS records to your company’s domain name.
How SPF, DKIM and DMARC records work together to prevent Email Address Spoofing (Source: Zimbra)
The Three DNS Records That Combat Email Address Spoofing
Adding SPF, DKIM and DMARC to a business’s domain name record is not as complicated as it sounds. In cases where your business uses Office 365 or G Suite you only need to follow the instructions set out below for your mail provider.
Creating an SPF record:
G Suite instructions
Office 365 instructions
Creating a DKIM record:
G Suite instructions
Office 365 instructions
Remember what we said about email having email sender addresses? We have yet to create one final record: DMARC. Contrary to popular belief, SPF alone cannot prevent spoofing. Without the DMARC record, cybercriminals can still forge the email address of your business as SPF is only verified against the invisible ‘envelope sender’, but not the ‘From:’ header. In other words, the criminals can spoof the sender’s email address, and it will still pass the SPF checks – and this is why you need the DMARC record.
You can use an online DMARC generator to craft the perfect DMARC record for your organisation, or you can just take our word for it and add the following DNS record to your company’s DNS. It is by no means perfect, but it is a great start:
_dmarc.mycompany.com.au. 3600 IN TXT “v=DMARC1; p=quarantine; pct=100;”
ANTI-PHISHING SERVICES TO DETECT EMAIL SPOOFING

There is another option to combat impersonation attacks. You can pre-screen your incoming emails using anti-phishing services. These services are designed to protect businesses from phishing threats.
Anti-Phishing services can analyze the content of the inbound emails and look for and indicators of a phishing attempt, such as wording and poor sender reputation. File attachments are also analyzed for known and unknown threats. the Anti-Phishing services are supported by Machine Learning, Artificial Intelligence, and Threat Intelligence Networks.
Anti-Phishing services are compatible with all email service providers.

